CentOS VM
Define the ssh key pairs used on Windows to connect the Azure VM using Putty with instructions located here.
Define the VM with the latest image of CentOS 7.6, Resource Group Py4SAS-vm, generate the ssh keys, and attach a 512GiB disk.
az vm create \
--resource-group Py4SAS \
--name Py4SAS-vm \
--image OpenLogic:CentOS:7.6:latest \
--size Standard_DS2_v2 \
--generate-ssh-keys \
--data-disk-sizes-gb 512
Returns:
{
"fqdns": "",
"id": "/subscriptions/e452751c-5818-4258-993b-247904c15f97/resourceGroups/Py4SAS/providers/Microsoft.Compute/virtualMachines/Py4SAS-vm",
"location": "eastus",
"macAddress": "00-0D-3A-17-8C-AD",
"powerState": "VM running",
"privateIpAddress": "10.0.0.4",
"publicIpAddress": "104.XXX.XX.XX",
"resourceGroup": "Py4SAS",
"zones": ""
}
Attach the disk to VM instance
az vm disk attach \
--resource-group Py4SAS \
--vm-name Py4SAS-vm \
--name Py4SAS-disk \
--size-gb 512 \
--sku Premium_LRS \
--new
ssh into the VM
ssh trb@104.XX.XX.XX
View file system before adding partition.
$ df -h
Filesystem Size Used Avail Use% Mounted on
/dev/sda2 30G 1.3G 29G 5% /
devtmpfs 3.4G 0 3.4G 0% /dev
tmpfs 3.4G 0 3.4G 0% /dev/shm
tmpfs 3.4G 9.0M 3.4G 1% /run
tmpfs 3.4G 0 3.4G 0% /sys/fs/cgroup
/dev/sda1 497M 65M 433M 13% /boot
/dev/sdb1 14G 41M 13G 1% /mnt/resource
tmpfs 696M 0 696M 0% /run/user/1000
Use the bash command fdisk to partition the disk.
(echo n; echo p; echo 1; echo ; echo ; echo w) | sudo fdisk /dev/sdc
Write a file system to the partition.
sudo mkfs -t ext4 /dev/sdc1
Mount the disk.
sudo mkdir /opt && sudo mount /dev/sdc1 /opt
Verify the mountpoint is available.
$ df -h
Filesystem Size Used Avail Use% Mounted on
/dev/sda2 30G 1.3G 29G 5% /
devtmpfs 3.4G 0 3.4G 0% /dev
tmpfs 3.4G 0 3.4G 0% /dev/shm
tmpfs 3.4G 9.0M 3.4G 1% /run
tmpfs 3.4G 0 3.4G 0% /sys/fs/cgroup
/dev/sda1 497M 65M 433M 13% /boot
/dev/sdb1 14G 41M 13G 1% /mnt/resource
tmpfs 696M 0 696M 0% /run/user/1000
/dev/sdc1 504G 73M 479G 1% /opt
Make the disk available after reboot. Return the UUID for the disk to mark an entry in /etc/fstab file.
sudo -i blkid
/dev/sdb1: UUID="f121de4a-765a-4e32-9bfa-733da972bbf1" TYPE="ext4"
/dev/sda1: UUID="7abf7f2c-6a8d-49de-9a87-3ff225f6e16a" TYPE="xfs"
/dev/sda2: UUID="08e9f7d6-7095-4811-af87-be3e4123c059" TYPE="xfs"
/dev/sdc1: UUID="9bd8ed43-b65d-47e9-b2dd-cbf896d80aaa" TYPE="ext4"
Add the following line into the /etc/fstab file.
UUID=9bd8ed43-b65d-47e9-b2dd-cbf896d80aaa /opt ext4 defaults,nofail 1 2
Install Azure CLI
Install the Azure command-line interface as an alternative to the web-based console.
Import the Microsoft repository key.
sudo rpm --import https://packages.microsoft.com/keys/microsoft.asc
Create a local azure-cli repository.
sudo sh -c 'echo -e "[azure-cli]\nname=Azure CLI\nbaseurl=https://packages.microsoft.com/yumrepos/azure-cli\nenabled=1\ngpgcheck=1\ngpgkey=https://packages.microsoft.com/keys/microsoft.asc" > /etc/yum.repos.d/azure-cli.repo'
Install Azure-CLI.
sudo yum install azure-cli
Login.
az login
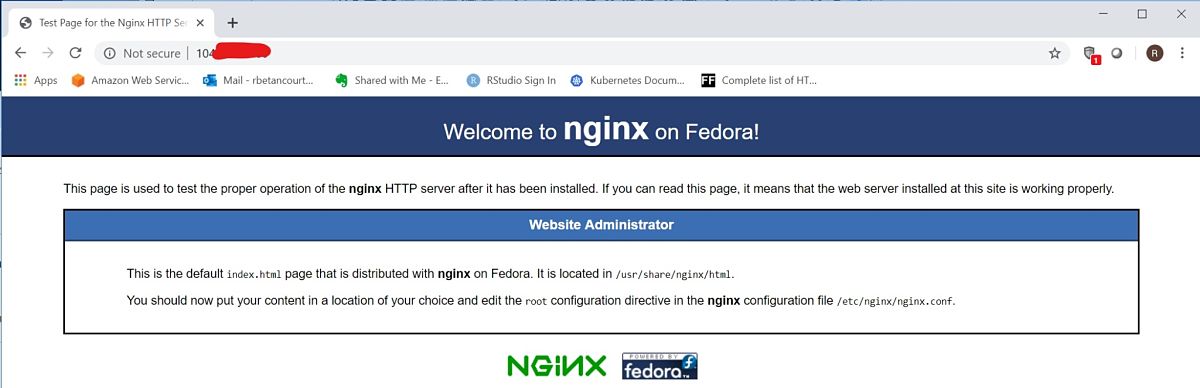
Install Nginx
Add CentOS EPEL package.
sudo yum -y install epel-release
Install Nginx
sudo yum -y install nginx
Start Nginx.
service nginx start
Open Ports
az vm open-port --resource-group Py4SAS --name Py4SAS-vm --port 80
{
"defaultSecurityRules": [
{
"access": "Allow",
"description": "Allow inbound traffic from all VMs in VNET",
"destinationAddressPrefix": "VirtualNetwork",
"destinationAddressPrefixes": [],
"destinationApplicationSecurityGroups": null,
"destinationPortRange": "*",
"destinationPortRanges": [],
"direction": "Inbound",
"etag": "W/\"32dea815-2aaf-468c-8bb9-93d57c1c1acd\"",
"id": "/subscriptions/e452751c-5818-4258-993b-247904c15f97/resourceGroups/Py4SAS/providers/Microsoft.Network/networkSecurityGroups/Py4SAS-vmNSG/defaultSecurityRules/AllowVnetInBound",
"name": "AllowVnetInBound",
"priority": 65000,
"protocol": "*",
"provisioningState": "Succeeded",
"resourceGroup": "Py4SAS",
"sourceAddressPrefix": "VirtualNetwork",
"sourceAddressPrefixes": [],
"sourceApplicationSecurityGroups": null,
"sourcePortRange": "*",
"sourcePortRanges": [],
"type": "Microsoft.Network/networkSecurityGroups/defaultSecurityRules"
}
Open a browser and test.
http://104.XXX.XX.XX:80